%20en%20seguridad.jpg)
In 2024, artificial intelligence trends in security companies and organizations are radically transforming the way this industry is operated. We are in an era where digital protection is not just a priority, but an essential component for sustainable progress and trust.
The constant evolution of cyber threats and the increasing amount of data shared online have elevated the importance of implementing advanced security solutions. Technologies such as real-time analytics, generative artificial intelligence and video analytics are now fundamental pillars for strengthening security in various industries, which not only address immediate risks: they also set a higher standard for protection and operational efficiency.
En este artículo, exploraremos las 5 tendencias de inteligencia artificial que marcarán una diferencia significativa en la seguridad en 2024 y más allá.
Table of Contents
- Trend 1: Generative Artificial Intelligence
- How do Generative AI systems work?
- 3 Industries using Generative AI
- Global Generative AI Market
- Trend 2: Drones
- How do drones work?
- 4 Drone applications in security
- Global Drones Market Forecast
- Trend 3: Video Analytics
- How does video analytics work?
- Applications of video analytics
- Global Video Analytics Market Overview
- Trend 4: Biometric Authentication
- How does biometric authentication work?
- Biometric Authentication Applications
- Global Biometric Authentication Market
- Trend 5: Cybersecurity
- How does cybersecurity work?
- 4 Cybersecurity functions
- Global Cybersecurity Market
Trend 1: Generative Artificial Intelligence
Generative AI is a type of artificial intelligence that is commonly used to create content in various forms, such as text, images, music, audios, and videos. This promising technology is based on the use of advanced artificial intelligence models, known as large-scale AI models.
These models have the ability to perform multiple tasks at the same time, such as generating summaries, answering questions, classifying information, among others. In addition, they can be customized for specific cases with minimal preparation and using very few data samples.
How do Generative AI systems work?
Generative AI systems employ a machine learning model to understand patterns and relationships in a dataset of content previously created by humans. They then use this pattern understanding to generate content autonomously.
A common technique for training a generative AI model involves the use of supervised learning, by providing the model with a dataset that includes human-created content, along with corresponding labels. From this dataset, the model learns to generate content that resembles human-created content and is associated with the same tags.
3 Industries using Generative AI
| Cybersecurity | Finance | Automotive Industry |
|
|
|
Generative AI has emerged as a key driver in the transformation of diverse industries, bringing significant innovations. from operational efficiency to improved safety and customer experience.
Below, we explore a few examples:
Cybersecurity
This technology has revolutionized cybersecurity by offering advanced threat detection capabilities, using generative models, it can anticipate and recognize patterns of malicious behavior, enabling rapid and proactive response to potential attacks.
Finance
In this sector, Generative AI has played a crucial role in fraud detection and prevention by analyzing large data sets to identify anomalous patterns, significantly reducing the risk of fraudulent activities.
Automotive
This industry has undergone an amazing transformation in recent years in manufacturing and safety processes. In testing the effectiveness of materials and manufacturing processes, they have been able to simulate various conditions and scenarios to evaluate the quality and durability of materials as well as vehicles.
Global Generative AI Market
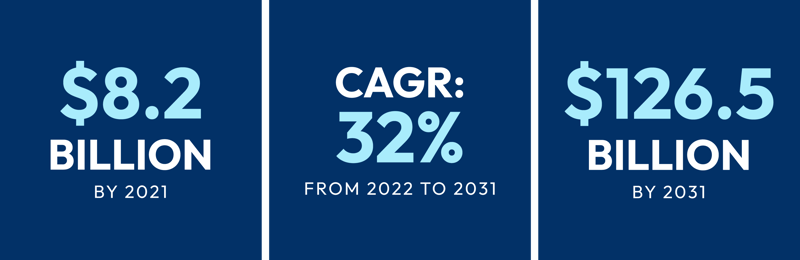 Source: Valuates Reports
Source: Valuates Reports
As we move into the next decade, it is clear that the influence of Generative AI will only increase as it is expected that by 2031, the global market will reach a value of $126.5 billion.
Trend 2: Drones
Drones, also known as unmanned aerial vehicles (UAVs), are remotely controlled aircraft, without the presence of a pilot on board, that have gained popularity in various industries thanks to their versatility and capabilities.
How do drones work?
Drones have the ability to move nimbly over uneven or rough terrain, overcoming obstacles, and offer the ability to capture images and other data from an aerial perspective.
This is possible thanks to the inclusion of cameras, sensors and other instruments that they can carry without posing safety risks to people.
Drones use electric motors that generate the power needed for flight. The motors are connected to propellers that provide the mechanism and steering to control them perfectly by remote control.
4 Drone applications in Security
| Search and rescue | Traffic control | Border surveillance | Airports |
| Reduces response times in critical situations. | Monitor the flow of vehicles providing essential data. | Provides a detailed and constant view of border areas. | Efficient inspections to detect potential threats. |
Search and Rescue
Drones allow to explore large areas quickly and efficiently, providing real-time images, access to restricted areas and even support in locating missing persons.
Traffic Control
Los drones ofrecen una perspectiva área para monitorear el flujo de vehículos en tiempo real, proporcionando datos cruciales para mejorar la gestión de tráfico, tener respuestas rápidas ante bloqueos o situaciones críticas.
Border Surveillance
Drones equipped with advanced technologies can detect suspicious movement patterns, improving the responsiveness of security agencies.
Airports
This technology has created efficient inspections when inspecting runways, lights and perimeter fences, including aircraft movement and critical area management, as well as tracking airport operations to help detect potential threats.
Global Drone Market Forecast
 Source: Business Research Company
Source: Business Research Company
The integration of drones into various applications has significantly evolved the security landscape, triggering a profound transformation in the way we address critical challenges. From search and rescue operations to border surveillance and military defense, these unmanned aerial devices have proven to be essential catalysts for security enhancement across diverse industries.
The exponential growth of the global drone market, according to The Business Research Company report, reflects the increasing demand and adoption of this innovative technology. The market size is projected to reach $52.21 billion by 2027, at a CAGR of 14.9%. This data underscores not only the widespread acceptance of drones, but also their crucial role in the ongoing evolution of security globally.
Trend 3: Video analytics
Video analytics, also known as video analytics or intelligent video analysis, is an advanced technology that uses specialized algorithms and software to analyze visual data. This technology uses image processing algorithms and machine learning techniques to perform these tasks, making it an essential tool in security, monitoring and real-time data analysis applications.
How does video analytics work?
Video analytics is based on an artificial intelligence training process, where data sets composed of images and videos are used to enable the system to identify objects, people and other relevant elements. Each image captured by the video analytics system is compared with a knowledge base containing definitions of critical events and suspicious behavior. In addition, this technology can generate alerts, notifications or reports when specific events are detected, enabling organizations to take timely action to ensure security and improve efficiency in their operations.
Video analytics emerges as a cutting-edge technology that goes beyond conventional observation and ushers in a new era of efficiency, security and intelligent operation in a variety of situations.
Applications of video analytics
In video surveillance networks it is difficult to see the full picture of what is being transmitted in a recording, so object detection is essential in security systems to identify and track vehicles, people or other elements in monitored areas, as well as for traffic monitoring, intrusion prevention and more to improve and support public safety.
El reconocimiento de patrones se aplica en entornos comerciales e industriales para optimizar operaciones, además, la detección de comportamientos sospechosos es crucial para resguardar áreas públicas y privadas para así poder alertar sobre posibles amenazas a las autoridades correspondientes.
These technologies have proven to be of great use to authorities by enabling them to detect objects, patterns and warn of suspicious behavior. An example of this is vehicleDRX, our AI video analytics product that not only detects and locates vehicles of interest, but also identifies suspicious behavior of individuals on motorcycles.
Learn more about our technology and how we contribute to strengthening the security of your city.
Global video analytics market forecast
This industry has experienced exponential growth in recent years, marking a milestone in the evolution of security and operational intelligence. However, its rise is far from reaching its peak; in fact, projections predict an even more dynamic and expansive future for this innovative market.
According to Fortune Business Insights, the global video analytics market size was valued at $6.86 billion in 2022 and is projected to grow from $8.27 billion in 2023 to $37.55 billion by 2030, showing a compound annual growth rate (CAGR) of 23.9% during the forecast period.
Trend 4: Biometric authentication
Biometric authentication, an established technique that has integrated big data and artificial intelligence over more than a decade, plays an essential role in fortifying security systems in both personal and enterprise devices. In its early days, it focused primarily on physical traits, such as facial dimensions or fingerprints; however, its evolution has been remarkable, especially in addressing protection against biometric data theft.
How does biometric authentication work?
Behavioral biometrics is based on the collection and analysis of data from everyday activities, such as typing on a keyboard, talking on the phone, using a mouse, or even using unique characteristics of our body. It is not limited to simply recognizing physical characteristics, but dives into the uniqueness of individual behaviors.
Initially, when you decide to use biometric authentication, the system registers certain unique things about your body, such as your face, your fingerprints, or as we mentioned earlier the way you type. These unique characteristics become your "biological password" which is securely stored in a device, similar to a digital safe, that only you can use or give access to.
Biometric authentication applications ?
Biometric authentication has been instrumental in a variety of industries, most notably in banking, healthcare and parcel transportation. This revolutionary method of identity verification not only improves security, but also provides a more convenient and efficient experience for users.
Today, in information security and financial data protection, biometric authentication can use unique features such as fingerprints, facial recognition and even retinal scans to ensure that only authorized users have access to their accounts and transactions to significantly decrease the risk of fraud and identity theft. ransacciones para disminuir significativamente el riesgo de fraude y robo de identidad.
This technology in the healthcare sector not only strengthens security and privacy, but also contributes to operational efficiency and improves the patient experience by ensuring fast and secure access to medical information.
Furthermore, biometric authentication adds an additional level of security to logistics operations, where the verification of the identity of package handling personnel through biometric traits ensures that only authorized persons are involved in package handling and delivery. This not only protects against theft and loss of goods, but also enables more accurate and secure tracking of shipments throughout the supply chain.
Global biometric authentication market
LThe growing need in security measures has created an extraordinary growth in biometric systems, projecting a significant increase. According to a report by The Insight Partners, the size of this market, which reached a value of $43 billion in 2021, is expected to reach a remarkable $85 billion by 2028.
This impressive growth is largely attributed to the increasing adoption of biometric authentication across a wide range of industries and applications. Biometric authentication, which uses unique physical or behavioral traits of an individual to verify his or her identity, has become a central element in digital and physical security.
Thanks to its ability to provide exceptional levels of security and convenience, biometrics is emerging as a crucial element in establishing secure and efficient environments in a variety of applications and industries on a global scale.
Trend 5: Cybersecurity
Also known as information technology (IT) security, it is the practice of protecting computer systems, networks, software and data against threats, attacks or unauthorized access. A field that has become a critical piece in the digital age, where information and critical operations are carried out through interconnected devices.
How does cybersecurity work?
Its operation is based on a combination of technological measures, processes and best practices to ensure information security, to safeguard the confidentiality, integrity and availability of information.
Cybersecurity begins with the identification of assets and vulnerabilities, followed by the implementation of protective measures, threat detection and incident response. It also addresses business continuity and recovery, including user education and awareness. Continuous improvement is essential, as cybersecurity is constantly adapting to evolving threats and technological changes.
4 Cybersecurity functions
| Cybercrime | Malware | Phishing | Cyberterrorism |
| Prevention and detection | Malware detection and removal | Anti-phishing filters and solutions | Threat monitoring and infrastructure defense |
Cybersecurity plays a critical role in preventing and detecting cybercrime, handling malware, protecting against phishing attacks, and defending against potential cyberterrorism threats.
Cybersecurity establishes proactive measures such as security policies, firewalls and intrusion detection systems for cybercrime prevention and detection to prevent unauthorized access and malicious activities.
For malware, cybersecurity uses anti-virus, anti-malware and advanced solutions to detect the presence of malicious software. Once identified, measures are implemented for effective removal, including the use of specialized tools and the application of security patches.
To prevent and reduce phishing, filters and solutions are implemented to block malicious messages and links. In addition to technological solutions, cybersecurity plays a crucial role in educating and raising awareness among users, providing information on how to recognize and avoid phishing attacks.
And for cyberterrorism, it constantly monitors cyber threats potentially related to terrorist motivations, uses intelligence and analysis tools to identify possible malicious activities that could endanger national security.
Global cybersecurity market
The global cybersecurity market has experienced substantial growth in recent years. In 2022 alone, the size of this market was valued at an impressive $153.65 billion. However, projections indicate a shocking increase, anticipating it to reach $172.32 billion in 2023 and expand further to $424.97 billion in 2030.
Several factors contribute to this growth. First, increased global connectivity and the expansion of emerging technologies, such as artificial intelligence, Generative AI and the Internet of Things, create a more complex landscape that requires advanced cybersecurity solutions. In addition, the growing awareness of the importance of protecting sensitive data and critical systems drives the adoption of cybersecurity solutions at the enterprise and government level.
As we have seen, the fusion of innovation and security has created technologies that have played a crucial role in our lives and industries. This technological advancement is not only about adapting to current threats, but anticipating and preparing for future challenges.
From video analytics to drones, these technologies have forged a path to a more secure and efficient environment. Their impact goes beyond mere protection; they have redefined the way we operate, improving not only security but also productivity and decision making.
Also learn how artificial intelligence algorithms are revolutionizing public safety here.